What is 2FA and how can I implement it?
2FA, or Two-Factor Authentication, is a security measure that provides an additional layer of protection to your online accounts by requiring two forms of authentication before granting access. It adds an extra step to the login process, making it more difficult for unauthorized individuals to gain access to your accounts, even if they have your password.
Typically, 2FA combines two of the following factors:
- Something you know: This is typically a password or a PIN.
- Something you have: This can be a physical device like a smartphone, a security token, or a verification code sent to your registered phone number.
- Something you are: This refers to biometric factors such as fingerprints, facial recognition, or iris scans.
Implementing 2FA usually involves the following steps:
- Enable 2FA: Start by accessing the account settings or security settings of the online service or platform you want to secure. Look for the option to enable two-factor authentication or similar terminology.
- Choose the authentication method: Select the preferred method for receiving the second authentication factor. The most common methods include text message (SMS), email, authenticator apps, or hardware tokens.
- Set up the chosen method: Depending on your choice, follow the instructions provided to set up the selected method. For example, if you opt for an authenticator app, you will typically need to download and install the app and then scan a QR code or manually enter a code to link it with your account.
- Verify the setup: Once the initial setup is complete, the service will usually provide a test code or send a test message to ensure that the second factor is working correctly. Verify that you receive the code or message and enter it as instructed.
- Store backup codes (optional): Some services may offer backup codes that you can use in case you don’t have access to your primary 2FA method. Store these codes in a safe place, like a password manager or a secure document.
- Use 2FA during login: From now on, whenever you log in to the service, you’ll be prompted to enter the second factor of authentication. Follow the instructions provided by the service to complete the login process.
It’s important to note that different services may have slight variations in their implementation of 2FA. It’s recommended to refer to the specific documentation or support resources provided by the service you want to secure for detailed instructions on enabling and setting up 2FA.
How To Fix Crowdstrike Blue Screen BSOD
If you are still experiencing issues with your computer, please follow these manual steps to regain access and functionality:
- Make sure you left your computer online for 60 mins or more at the blue screen stage and manually rebooted. If you are still receiving a blue screen then you will need to manually fix the issue.
- Please watch this instructional video: it will assist you restoring your computer – https://www.youtube.com/watch?v=ntZv5ZKusb0
- The most important element is to get your PC to boot into SAFE MODE. Different brands have different ways to do this and you can google how to navigate your brand and model.
If you are unable to get to the screen needed, try these steps:
- Reset your PC by holding down the power button for 10 seconds and then press again to power on.
- For most laptops you can press F8 continuously the moment the PC starts up and find run in Safe Mode
- For some Lenovo laptops, press Enter to interrupt startup the moment the Lenovo screen pops up.
- Press F11 to recover your system key and follow the above video steps.
If you require a BitLocker Code, please follow these steps to access your Microsoft Account recovery keys:
- Open a web browser and go to https://account.microsoft.com/account – You can do this from another laptop or your phone.
- Click Sign in and enter your email address and password.
If you have forgotten your password, please RESET your password – if you cannot remember your email address try your mortgagechoice.com.au or smartline.com.au email or your personal email address. (This account is where you would have subscribed to Microsoft Home for eg. to subscribe to Word and Excel.) - Scroll down to Devices and then click View details for the device requesting the recovery key.
- Click Manage recovery keys.
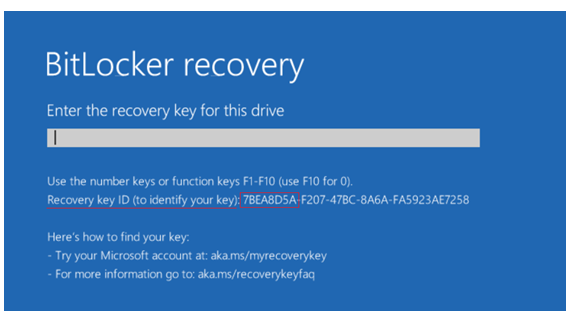
- Reference the Key ID from the BitLocker recovery event screen to locate the appropriate recovery key.
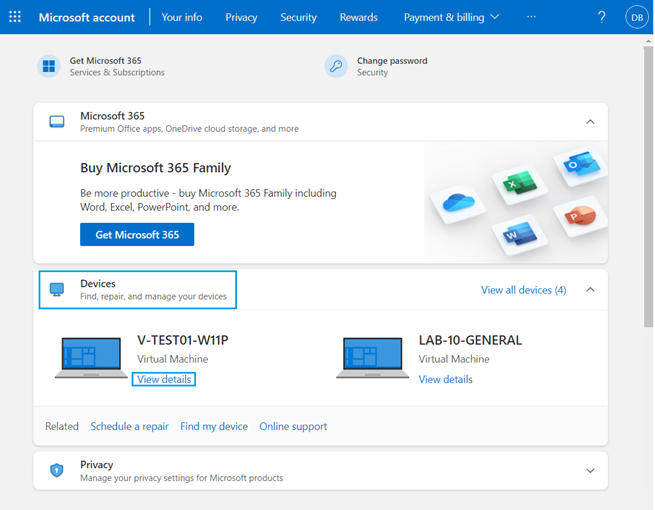
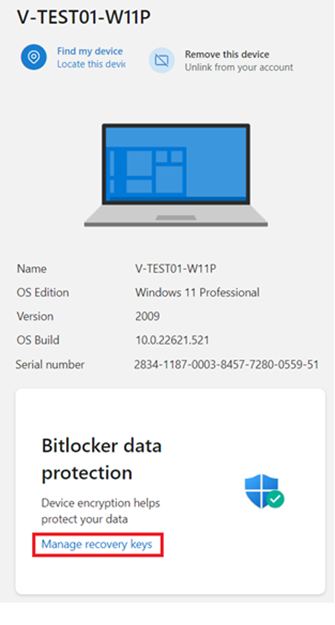
Please ensure that you have identified the Key ID (highlighted in red below) from the BitLocker recovery event screen to locate the appropriate recovery key.

Once you have located the correct code, please write it down and then enter it on your affected device and follow the video instructions for booting into SAFE MODE.
Phishing Attacks
| Scammers will try phishing attempts across emails, text messages, direct messages on social media, and phone calls. Any unsolicited email, phone call or direct message should be treated with suspicion. Being suspicious is a good thing and team members should be encouraged to: STOP, CHECK & PROTECT 🛡️ STOP – Don’t be rushed into clicking a link, downloading software or providing personal or financial information. 🛡️ CHECK – Verify who you are talking to. Call your IT support or financial institution on a number you have sourced independently. 🛡️ PROTECT – Act quickly if you have provided access to private information. Contact your bank immediately and report to scamwatch.gov.au to help protect others. If you have an IT supplier, be clear about when, where and how your team might receive official help so you can recognise legitimate advice from the scams. |